Intelligent Video Surveillance Setup Guide, Intelligent Video Surveillance (IVS), also known as intelligent video monitoring or intelligent CCTV, represents a significant advancement over traditional surveillance systems.1 It leverages cutting-edge technologies like Artificial Intelligence (AI), machine learning, deep learning, and computer vision to automatically analyze video footage in real-time or from recordings.2
Here’s a breakdown of what makes IVS “intelligent” and how it works:
Key Differences from Traditional Surveillance:
• Proactive vs. Reactive: Traditional systems primarily record footage for later review, acting as a reactive tool for forensics. IVS, however, actively analyzes video in real-time, enabling proactive threat detection and immediate responses.3
• Automation vs. Manual Monitoring: Traditional surveillance heavily relies on human operators to constantly monitor feeds, which can be prone to human error and fatigue.4 IVS automates many of these tasks, reducing the need for constant human supervision.5
• Analysis vs. Recording: IVS goes beyond mere recording.6 It interprets and understands the visual data, identifying patterns, behaviors, and anomalies that might indicate security threats or other events of interest.7
How Intelligent Video Surveillance Works:
1.Data Collection: High-definition cameras, often equipped with advanced features like night vision and wide dynamic range, are strategically placed to capture clear and detailed footage.8 These cameras may also integrate with other sensors (e.g., motion, thermal, audio) for richer data.9
2.Powerful Analytics Engine: At the core of IVS is a powerful analytics engine that uses AI and machine learning algorithms.10 This engine processes the vast amounts of video data collected by cameras and sensors.11
3.Real-time Analysis: The algorithms analyze video feeds in real-time to:12
◦ Detect and Classify Objects: Identify and categorize objects like people, vehicles, animals, or specific items.13
◦ Motion Detection: Differentiate between significant movements (e.g., a human intruder) and irrelevant ones (e.g., swaying trees, animals), reducing false alarms.14
◦ Behavior Analysis: Recognize unusual or suspicious behaviors, such as loitering, running, unauthorized access, or the presence of abandoned/missing objects.15
◦ Facial Recognition: Identify individuals by their facial features, often by comparing them against a database.16
◦ License Plate Recognition: Read and record vehicle license plates.17
◦ People Counting: Count the number of people in a specific area.18
◦ Crowd Management: Monitor crowd density and dynamics to spot potential dangers or congestion.19
4.Anomaly Detection: IVS systems “learn” what constitutes normal behavior and patterns. When an anomaly or something breaks the established pattern, it triggers an alert.20
5.Alerts and Actions: Upon detecting a predefined event or anomaly, the system can automatically:
◦ Send alerts and notifications to security personnel (via email, SMS, etc.).21
◦ Trigger alarms.22
◦ Initiate recording.
◦ Activate other security systems (e.g., access control, lighting).23
◦ Provide real-time situational awareness for a swift response.24
6.Data Management and Insights: IVS systems can store and manage large volumes of video data, extracting valuable metadata for enhanced search capabilities, streamlined video management, and generating insights for better decision-making (e.g., optimizing store layouts in retail, traffic management).25
Key Features and Applications:
• Enhanced Security: Proactive threat detection, intrusion detection, auto-tracking of suspects, and reduced false alarms.26
• Public Safety: Monitoring public spaces, crowd control, traffic management, and incident detection.27
• Retail: Customer behavior analysis, optimizing store layouts, inventory management, and shoplifting detection.28
• Industrial and Critical Infrastructure: Perimeter security, predictive maintenance by monitoring equipment, and compliance monitoring.
• Smart Homes/Businesses: Remote monitoring, alerts for unusual activity, and integration with other smart devices.29
By transforming raw video data into actionable insights, Intelligent Video Surveillance significantly enhances security, safety, and operational efficiency across various sectors.30
.
.
How to Set Intelligent Video Surveillance Function (WEB 5.0)
1.Product Model and Firmware Version
Any model and firmware with IVS supported. (This tutorial is based on WEB 5.0 firmware)
Interface may vary on some models and firmware.
1.Operation Description
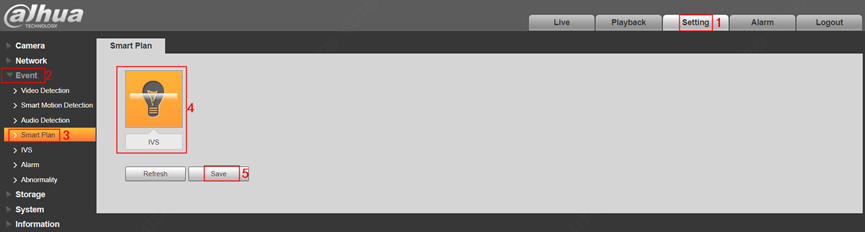
2.Login Device.
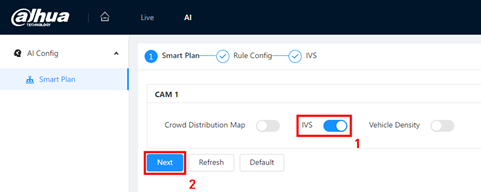
3.Enable IVS in AI – Smart Plan.
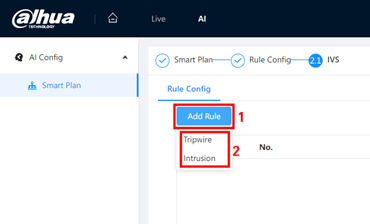
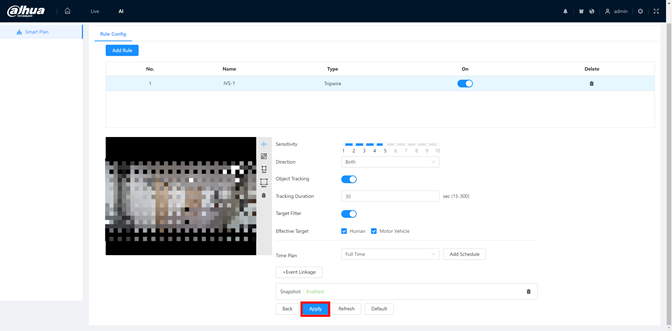
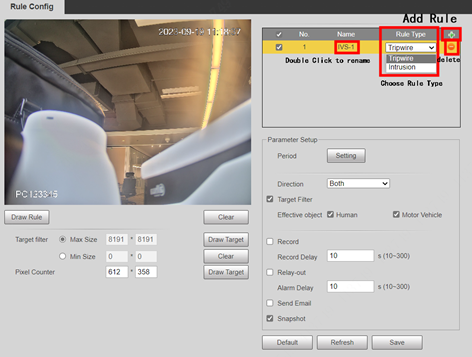
1.Click Add Rule button to add a new rule and select the IVS rule type.
1.Click Draw Rule Icon to set the rule region / line.
Click rule name can modify it. Click the icon can delete this rule.
Use left click on the image to draw the rule, right click to end the drawing.
Regional rules will auto close into a region when finished drawing.
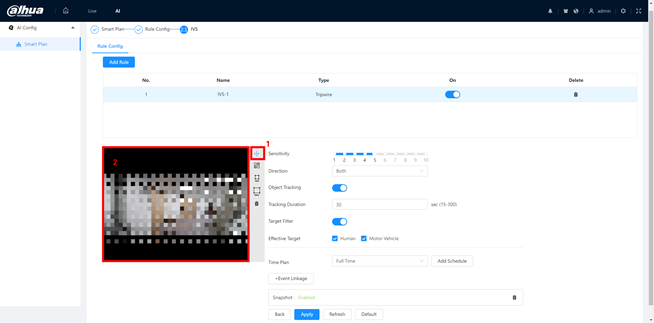
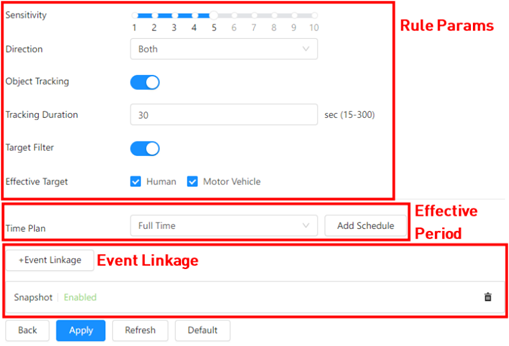
1.Set parameters of current rule.
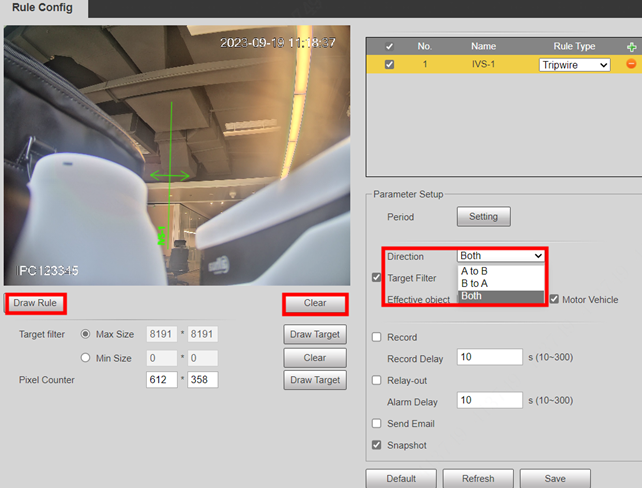
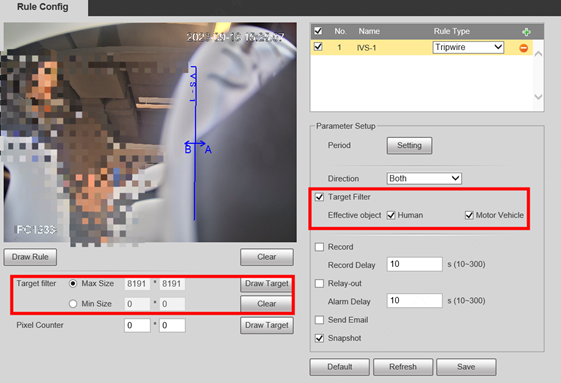
Rule Params: You can set the rule effect period, detection direction, sensitivity and enable special target filter. Different rule type may have different rule params.
Effective Period: You can select Effective object, Human or Motor Vehicle. For example, when you select Human as the alarm target, an alarm will be triggered when the system detects that persons trigger the rule.
Event Linkage: You can select what operation will be done when event triggered.
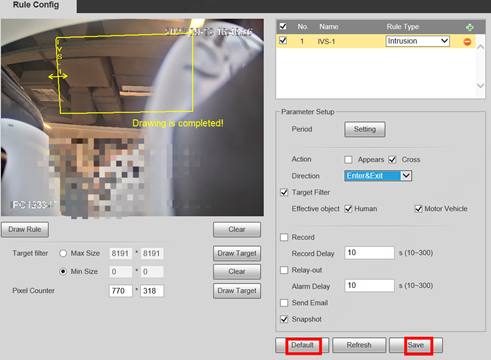
1.Click Save to apply the rule. Or use Default to clear IVS settings.
.
How to set Intelligent Video Surveillance (Web 3.0)
1.Product Model and Firmware Version
Any model and firmware with Intelligent Video Surveillance supported. (This tutorial is based on WEB 3.0 firmware)
Interface may vary on some models and firmware.
1.Operation Description
2.Login Device.
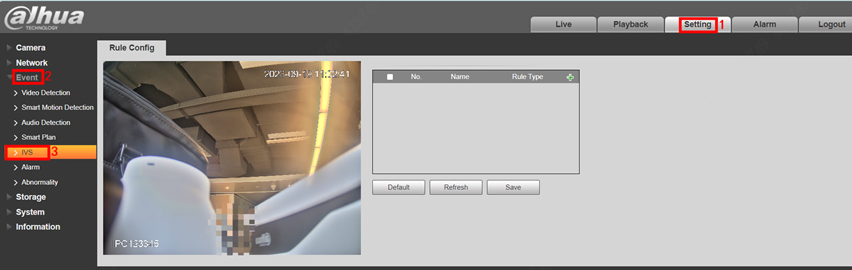
3.Select Setting > Event > Smart Plan > IVS > Save.
.
1.Select Setting > Event > Smart Plan > IVS > Save.
.
1.Click to add a new rule.
Double-click the Name to modify rule name, and select the Rule Type you want, also you can click to delete it.
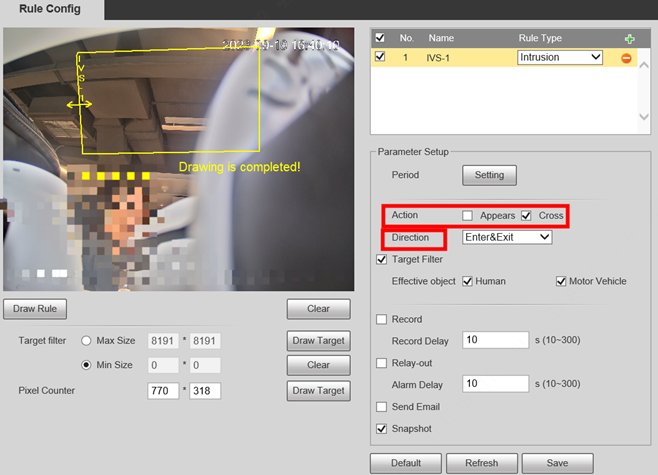
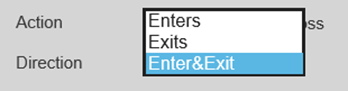
1.Click Draw Rule to draw a detection line or area in the image, Right-click to finish drawing. And set the Direction of rule detection.
Function 1: Tripwire
And you can click Clear to delete all drawn lines.
Function 2: Tripwire
.
And you can click Clear to delete all drawn lines.
1.Enable the Target Filter.
You can select Effective object, Human or Motor Vehicle. For example, when you select Human as the alarm target, an alarm will be triggered when the system detects that persons trigger the rule.
Click Draw Target to draw the minimum gathering area in the scene. The alarm will be triggered when the number of people in the detection area exceeds the minimum area. When the rule of crowd gathering is configured, you do not need to set target filter, but draw the minimum gathering area.
Click Clear to delete all drawn detection lines.
.
Click Draw Target at the right side of Pixel Counter, and then press and hold the left mouse button to draw a rectangle, the Pixel Counter then displays its pixel.
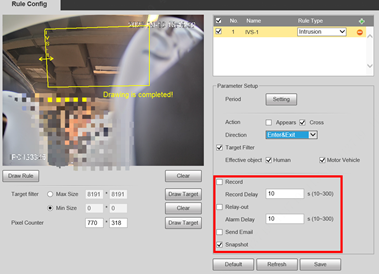
1.Enable the event linkage.
1.Click Save. Or use Default to restore all settings.
Construction Instruction Maanual_DH Network Camera_Installation Manual(AI Fisheye)
.
Scenario Requirements
Specific requirements:
12.Scenario requirements: This device is suitable for various indoor and outdoor scenarios with demands on waterproof, IR and high resolution, such as hall, warehouse, canteen, exhibition hall, supermarket, subway platform, square, school gate, and high-altitude panorama.
13.Recommended scenarios: The economical fisheye network camera is mainly used in retail scenarios such as small shops and small supermarkets, and the number of people in the arming region shall be less than 35.
Installation Requirements
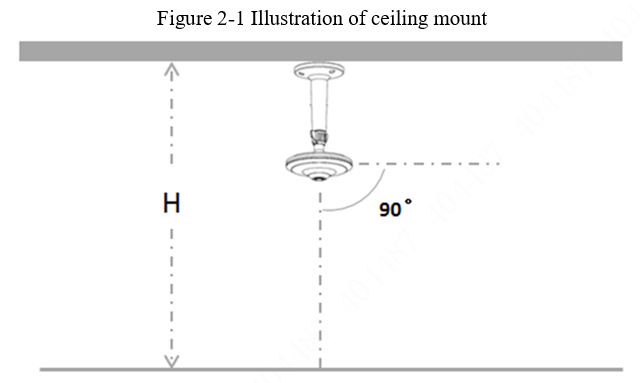
For ceiling mount mode, see the following installation requirements:
1. There is sufficient light in the scenario to ensure illumination effect.
2. Avoid a complex scenario with frequently changing light, backlight, and direct light exposure.
3.mountMake the camera face the monitoring center region, so that the intelligent detection will be more accurate. See Figure 2-1.
4. The recommended installation height (H) is 3–4 m. Exceeding this range will affect the accuracy
Installation
• Ceiling Mount
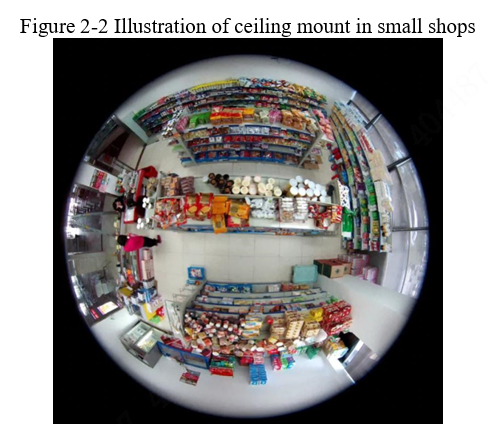
The surveillance image of fisheye products is an original circle and is wider. You need to use multiple devices to monitor a scenario, but one fisheye camera can do this. Use this advantage during installation. In view of the advantages, the ceiling mount is preferred for indoor installation. See Figure 2-2, the small shop is equipped with a ceiling mounted fisheye camera
.
Generally, the indoor floor is 3-4 m away from the ceiling and this height is proper for the economical fisheye cameras. Install the cameras in the middle of the monitored places, thus making the monitored places in the middle of the fisheye cameras, and obtaining most effective images. The project indoor products can be installed higher (6-8 m).
• Wall Mount
Wall mount is needed based on different customer requirements or scenarios. The height selection is vital to wall mount. The mount height might vary according to main surveillance scenarios. If too high, the ceiling is included in the image. See Figure 3-3, the indoor fisheye camera is mounted too high, leading to less effective images.
Therefore, for indoor wall mount, the camera should not be installed too high. Generally, 2-3 m is preferred.
.
Indoor Environment
It is necessary to select proper indoor fisheye products and well install them. The indoor products are not subject to waterproof or explosion proof requirements. Therefore, refer to this for model selection.
• IR Notes
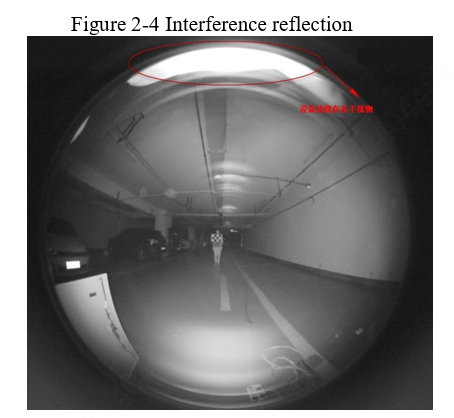
IR devices are less dependent on the environment, so they can perform surveillance efficiently in the dark. In addition, install IR devices against interference from other objects. The fisheye lens enjoys a wide field, so IR reflection will largely affect the image effect. See Figure 2-4, IR reflection occurs when a hand touches the front cover surface during the image shooting test, resulting in abnormal images.
Outdoor Environment
In the outdoor environment, ceiling and wall mount are preferred, not ground mount.
The ceiling mount is generally 6-8 m. For example, the camera installed at the height of 8 m has a wider view than that installed at the height of 6 m. For road panoramic surveillance, see Figure 2-5.
.
Unlike indoor, the outdoor wall mount depends more on the mount bracket than the height. The figure below shows the outdoor wall mount scenarios – monitored gateway and roads.
Arming Data
For fisheye products, the closer to the edge, the greater the distortion of the image, thus the intelligent detection rate of the region close to the image edges reduces. To ensure the effect of intelligent detection, pay attention to the following points when enabling the function:
1. There is sufficient light in the detection image without obstacles.
2. The detected person must be fully exposed (such as the shoulder width).
3. It is recommended that the detection region is within 80% of the image center.
4. The lens surface is free of obstruction, dirt, and other factors that affect the image.
.
Table2-1 Reference data for EW5541/EB5541 fisheye arming
| Product Model | Focal Length (mm) | Recommended Installation Height Range (m) | Person Height (m) | Installation Height (m) | Surveillance Radius (m) |
| DH-IPC-EW5541 Series DH-IPC-EB5541 Series | 1.4 | 3<H<4 | 1.7 | 2.5 | 4.3 |
| 1.7 | 3 | 4.2 | |||
| 1.7 | 3.5 | 4 | |||
| 1.7 | 4 | 3.7 | |||
| 1.7 | 4.5 | 3.4 |
.
Table2-12Reference data for EBW81242 arming
Note: Surveillance radius is the effective detection width corresponding to the central axle of the camera. Do not mistake it for the detection width of the farthest end or nearest end of the camera.
Table 2-2 Arming reference data for EBW81242, EBW81242-AS-S2, and EBW8842-AS
| Installation Height (m) | Intelligent Function | Inspection Region Radius (m) |
| 3 | People counting | 5 |
| Queuing time | 4 | |
| 3.5 | People counting | 5 |
| Queuing time | 4 | |
| 4 | People counting | 5 |
| Queuing time | 3.5 |
Table 2-3 Arming reference data for EBW81242-AS-IVC and EBW8842-AS-IVC
| Installation Height (m) | Intelligent Function | Inspection Region Radius (m) |
| 3 | People counting | 4.5 |
| Queuing time | 3.5 | |
| 3.5 | People counting | 4.5 |
| Queuing time | 3.5 | |
| 4 | People counting | 4 |
| Queuing time | 3 |
.
.